Entropi Encryption
Overview of the Program
After several dubious attempts to create a strong encryption program, the Entropi encryption algorithm was conceived. To counter the vulnerabilities found in earlier attempts, several strategies were employed. The encryption process takes place in two dimensions, rather like a cross weave pattern. The employment of pseudo randomly selected replacements, combined with a unique method for creating pseudo chaotic strings, produces an order of complexity which is difficult to assess.
The program only works with ASCII characters. The extended ASCII character set is also supported, although the main purpose of the program is to encrypt English text and numbers. Passwords can be made up of any combination of printable characters; so you could use a sentence, or include symbols and punctuation marks. Brute forcing a long password of this nature would be an extremely painstaking procedure and could take many years. NOTE: To ensure a strong encryption, the letters in the password should appear in non-alphabetical order. It also helps if you repeat a few characters.
| Screenshot |
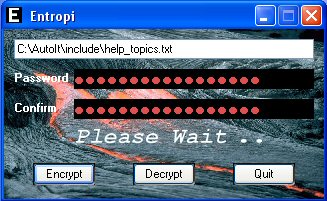
|
What is the Nature of an Entropi Encryption?
The sample below is an encryption of the following well known phrase repeated ten times:
'a quick brown fox jumped over the lazy dog'
5k3xaj25ltacncg1tuii2q4j54nblmtwxro7l5e7l7p78vpne5571u3dkqbcwngj56hwfdutgoc912jj1q9v
wpvnw5htxvkng6ya1uxpmv3dmmzyet33ykctvpkn8te3wx7ssns2vqbx62aclfzaa7r6kon1smv35fnv3pej
a2ieygmqs42ay7kg4geiinlknij4kcl3b885cajaubfgi8pkhzcg76z8uzwav2v5g8yrmuevnw5ht2zpn5yy
2gmp6zwgycih7q8erm2qzmplxmi3e7vukeuxrpw5mu3x2vuwiz6358fzbcgnv4u3z738rtpsc9st39enu688
5rni34jlj46p78qkkbo57c7epmvv1gcayet1lfdigeyq9fbdh1qz7b2p3aj25wgb1mixa53zc6z1a54j2mxf
6mkvfdiieytfyicaen7s5kceskaubfb14rg16v9bko1fsmz4foabxrp74j75kgnnz7woihgu8erdmv3da7zy
niwxpqjd29bzbx4jb11fpoepqgko1aya8oriwpgfeycmyj8qnn49ezlub2tna9kq6jkqzy56tofd11wmtf9x
iki3t8al583kg5o8v8wcm57sy3dgm6j18od563j38k1hnkn9rgk1qjy5kczvq414jac4caii5zgzdfuzwsjr
m2yetepge116gq9cx1eclgob233mpwoltgiag7qfozgkok13x98l8gn1eqpdshokg5ovvkkuwyac754fzbc2
skl7fqxntslxzcu5koutbij22v5gxrsd1oyj465o2zgng6yalygjkqmlzmw37kogykdf2lc9t5gkdoz7jd92
Despite the fact that the plain text is comprised of the same phrase repeated ten times, it can clearly be seen that each line of the encryption is different. If you were to use the same password to encrypt the same message again and again, the result would be different each time. The only drawback to this is that using the same password to produce several encryptions of the same text may present potential hackers with too much information. Providing you avoid creating such duplicates, this weakness can never be exploited.
Additional Information
Entropi was only designed to encrypt small to medium sized text files. It would probably be too slow for anything on a larger scale. Some analysis has been done during testing, and the results would indicate that encryptions of up to 200,000 characters are impenetrable to frequency analysis. Much larger amounts of data can probably still be encrypted with impunity, although theoretically a longer encryption could leak small amounts of information. Whether such leaks are critical is an open question. They may simply introduce greater ambiguity due to the nature of the cipher. Personally I wouldn't attempt to crack an Entropi encryption.

|
DELETED THIS PROGRAM HAS BEEN REMOVED BY THE AUTHOR |
Please read the release notes in the zip file before running the program. For anyone who is interested, the source code is available at: http://www.autoitscript.com/forum/index.php?showtopic=116162